 Ransomware Disguised as Invoice Email
Ransomware Disguised as Invoice Email
Email has become one of the most common ways for ransomware to make its way into your system.
Hackers are constantly trying to trick us into giving them access to sensitive information, and invoice phishing scams are growing in popularity. For example, the PyLocky ransomware delivered via email regarding invoicing. Some of the more sophisticated scams deliver a phishing email, and then use social engineering via phone call to obtain more information.
With this rise in the frequency of ransomware attacks, it is more important than ever to be well informed on how to combat it.
In this post we will look at how you can recognize ransomware that is disguised as an invoice email.
Here are three easy steps to validate whether or not the email is legitimate. It is as simple as hovering your mouse over a few key places to review pertinent information.
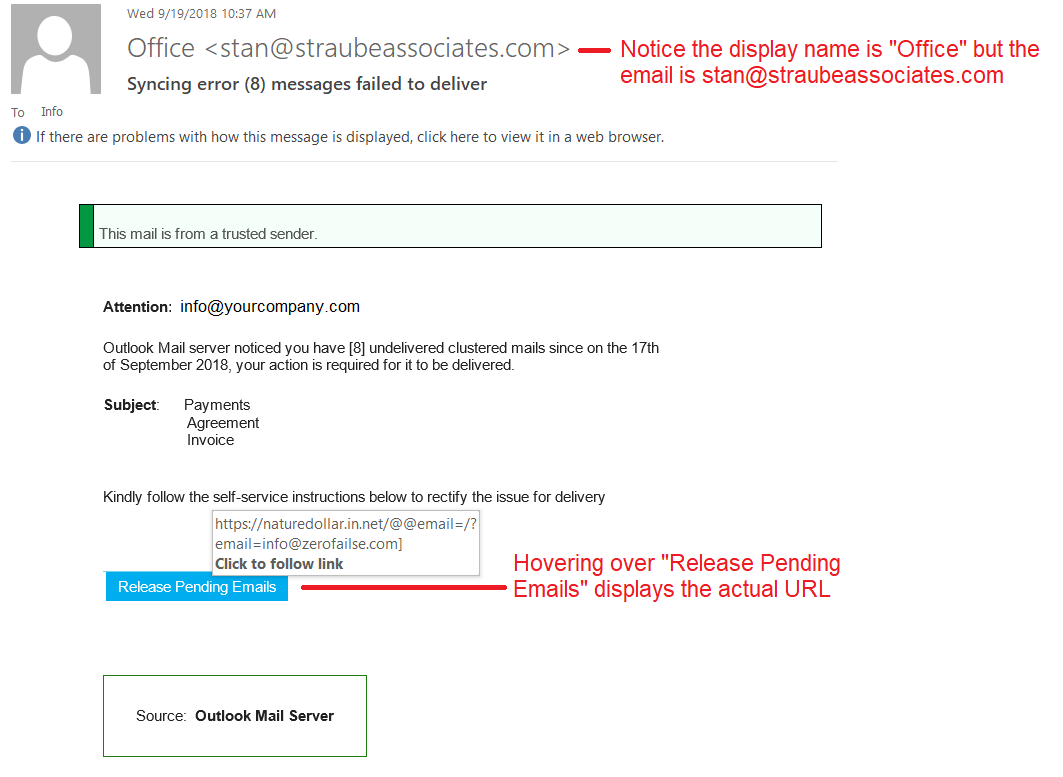
Below is a screenshot of a phishing email to help explain where you should be looking.
- Do you know the sender? Upon reviewing the email header, notice the display name is “Office” but the email address is stan@straubeassociates.com. Typically, the display name should be the same as the email address or the person’s actual name.
- Are you expecting what is requested in the email? Most people utilize Microsoft Office365 as their email provider. In addition, most businesses have an IT support services provider to manage email so you as a user would not receive an email about undelivered emails.
- Where do the hyperlinks actually go? Simply hover over the call to action that has the hyperlink to see where it is trying to take you. In the example below you are being redirected to naturedollar.net which definitely has nothing to do with undelivered emails.
If you are unsure whether or not the email is a phishing scam you can always take a screenshot and send to your IT department. Do not forward the email because it notifies the hackers that your email account is valid.
To take a screenshot:
Windows: CTRL + PrtSc or Windows Key + FN + Spacebar
Apple: Command + Shift + 3 or Command + Shift + 4
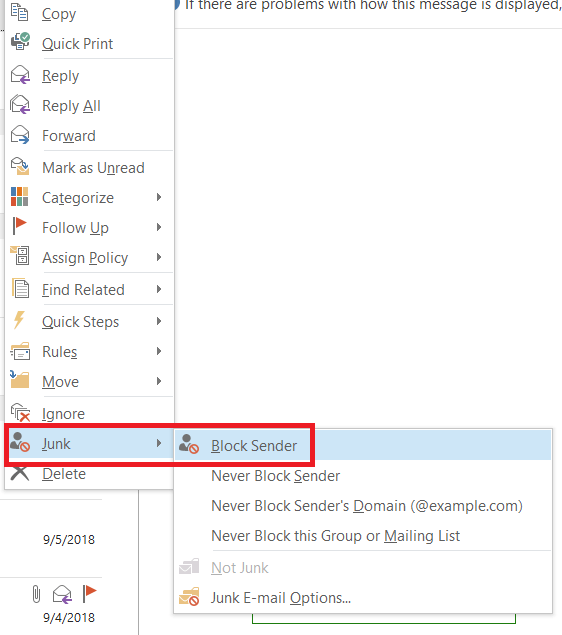
If you know the phishing email is junk email simply right click on the email in the message list > select Junk > Block Sender.
Ransomware attacks can be devastating to any business, and the methods hackers use are becoming more sophisticated. Use the information above to prevent the problems before they happen.
If you’re concerned about ransomware or other cyber-attacks on your business, Wolf Technology Group can help! Don’t leave the security of your business to chance. Schedule your Security Health Check today.

 Ransomware Disguised as Invoice Email
Ransomware Disguised as Invoice Email