How to Avoid Phishing Scams
It is easy to become the victim of a phishing scam if you are not careful online. Hackers are become more and more sophisticated with their attacks. Criminals are constantly trying to scam us via phone calls, emails, text messages (SMS) and now social media (Facebook, Snapchat, etc.). However, there are three simple steps you can take to protect yourself. Continue reading to learn how to avoid phishing scams.
October is National Cybersecurity Awareness Month (NCSAM), and as such, we encourage employees, vendors, friends, and family to take proactive steps to enhance personal and collective cybersecurity. NCSAM is a collaborative effort between government and industry to raise awareness about the importance of cybersecurity and to ensure that all Americans have the resources they need to be safer and more secure online. Wolf Technology Group is a NCSAM Champion helping to increase awareness and can assist your business with cybersecurity best practices
What is Phishing
Phishing is when a cyber criminal impersonates another company trying to get users to provide sensitive personal information. For example, an email from Chase Bank asking you to click here to login to your account because there is an issue. The link may contain a virus or trojan horse that installs a key logger to track what you type to try and steal sensitive information. The key logger can obtain the passwords you use and since many people reuse passwords it can make it fairly easy for cyber criminals to login to your accounts.
One: Attachments and Links
So many emails are received daily from various sources. The easiest way to protect yourself from phishing scams is to avoid opening attachments or links from unknown senders. Many of the phishing scams are obvious, but others are difficult to identify.
For example, if you receive an email or text from Chase Bank, but you do not have an account with them you know it is a scam. There are other indicators like the email from name versus the actual email address. The screenshot below provides additional helpful information. If you receive a notification from a company that you have an account, you should never click on the link from an email or text. Always go directly to the company’s main website to login.
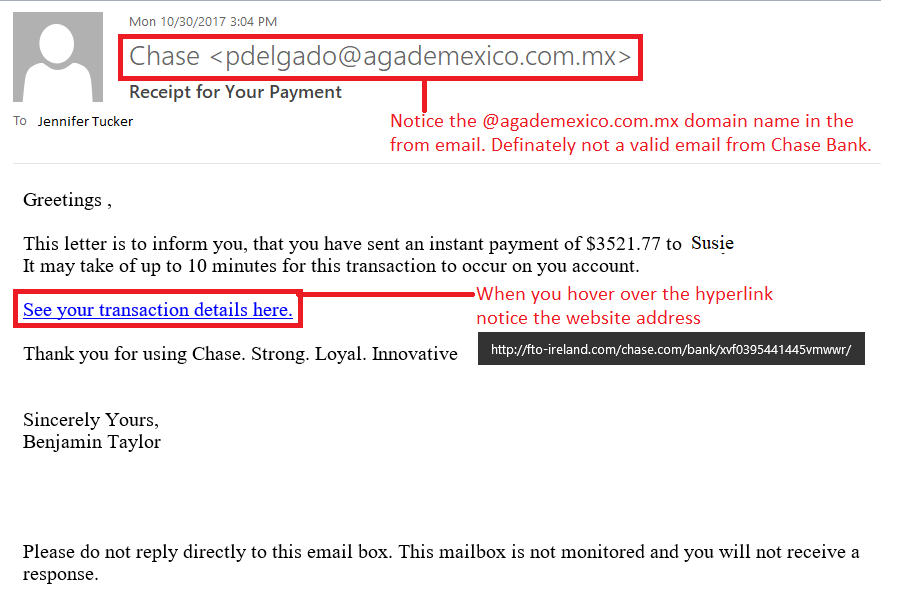
Two: Contact Sender
It only takes a few minutes to contact the sender to verify whether the message was valid. Setup a process and ensure the appropriate parties are trained. For example, important matters such as financial transactions the best practice is to require phone call verification once an email is received. In addition, there should be designated individuals that are authorized to make financial transactions to prevent fraud. Remember, if the email seems odd it is best to take the time to verify rather than having to deal with a cybersecurity incident.
Three: View URL
Hovering over URLs in a message can save you and your company a huge headache. Clicking on URLs can enable scripts to run that launch malware that can infect your company network encrypting data, holding it hostage. Last year, the City of Atlanta was infected with ransomware demanding $52,000 to get their data back. They ended up spending $2.6 million. The best defense against cyber threats is educating users and having good backups located offsite.
Here is another phishing example from one of the most widely-used software companies, Microsoft.
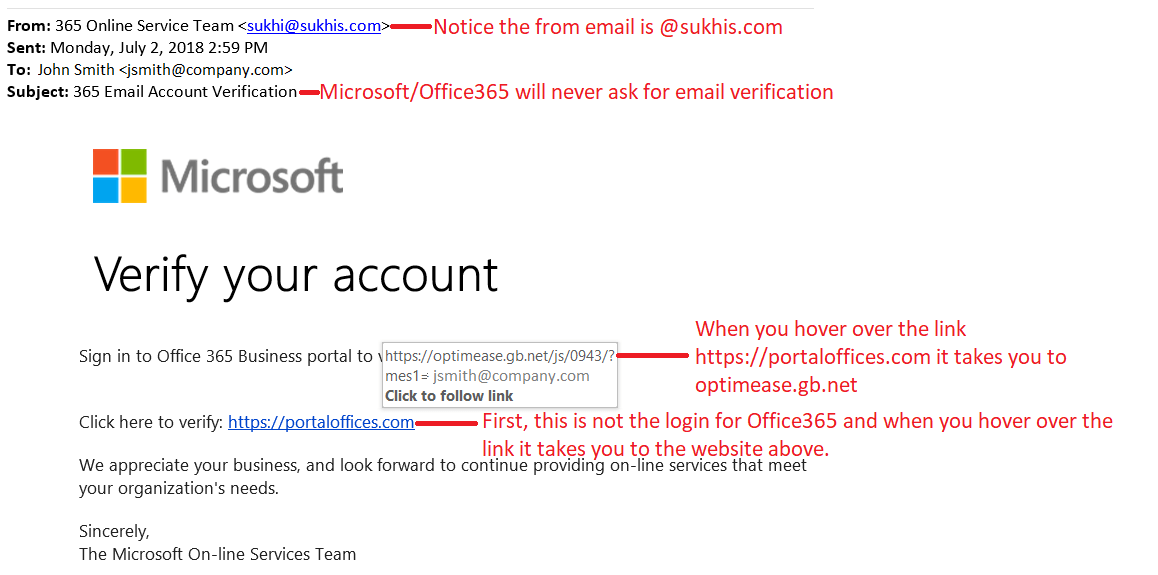
We must work together, and all do our part to help build a more secure cyber world. Learn how you can be cyber smart this National Cybersecurity Awareness Month at staysafeonline.org. Schedule your free intrusion test today for your business or contact Wolf Technology Group to learn how we can help keep your business secure. We provide full-service IT support from cybersecurity to user support. Learn more about our Managed IT Services.
Tags: Cybersecurity, National Cybersecurity Awareness Month, NSCAM, Phishing